
Reach Security Excellence with SOC Powered by GRC³
AI algorithm makes real time mapping, leveraging controls testing, real time visibility, and managing task seamless. Avoid duplication of tasks.
GRC³ is comprehensive and scalable single platform to comply, audit, and manage SOC1, SOC2, SOC for Cybersecurity, and SOC for Supply Chain.
Request a DemoSave Time by Automating SOC 2
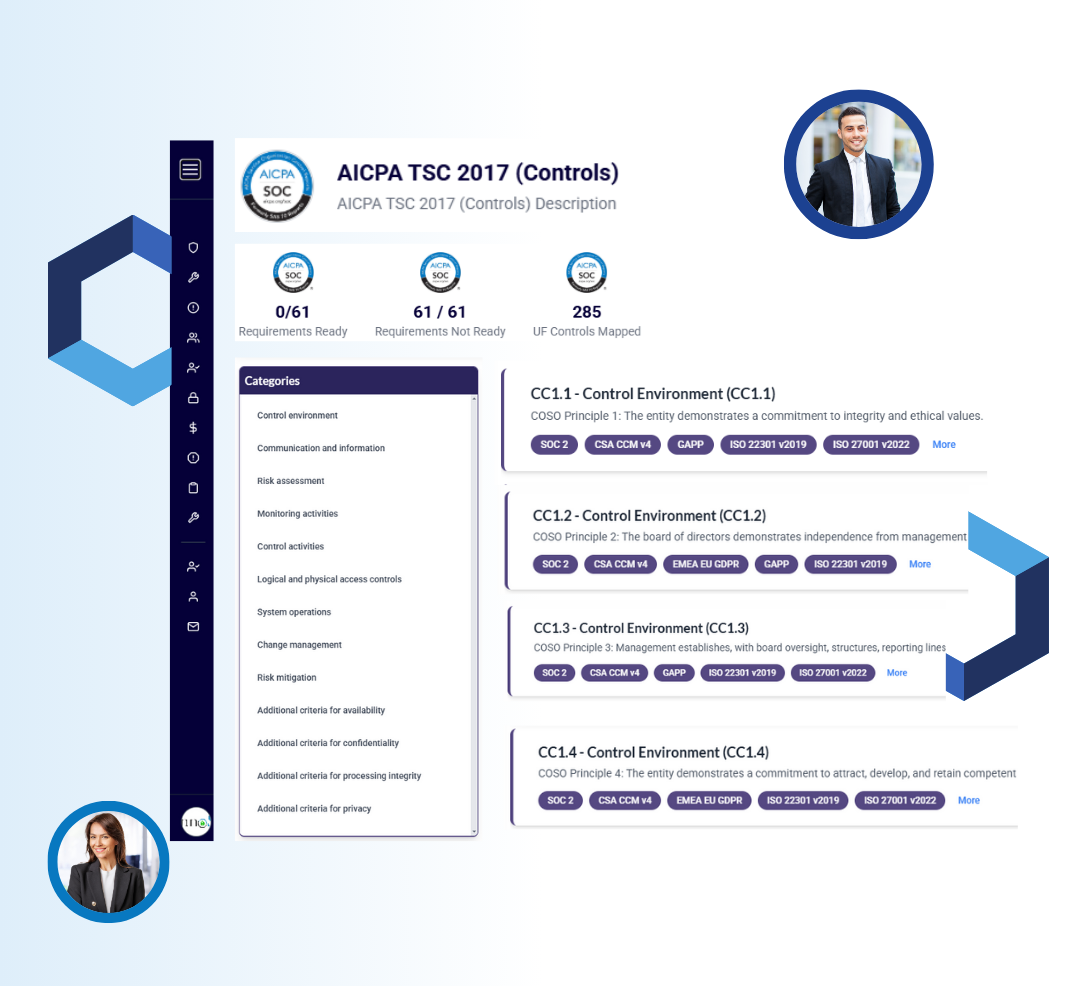
All in once place - GRC3 makes SOC compliance to focus on compliance work
SOC 2 reports follow the Trust Service Criteria (TSC), which cover security, availability, processing integrity, confidentiality, and privacy. GRC3 is the ONLY SOLUTION PROVIDER who has all modules supporting TSC compliance on one single platform.
No more templates or manual mapping
AI algorithms facilitate real-time mapping of controsl, leverages controls testing to avoid duplication of evidence collection taks, provides real time visibility, and ensures seamless task management. GRC³ allows you to quickly assess your compliance readiness as you think of new compliance.
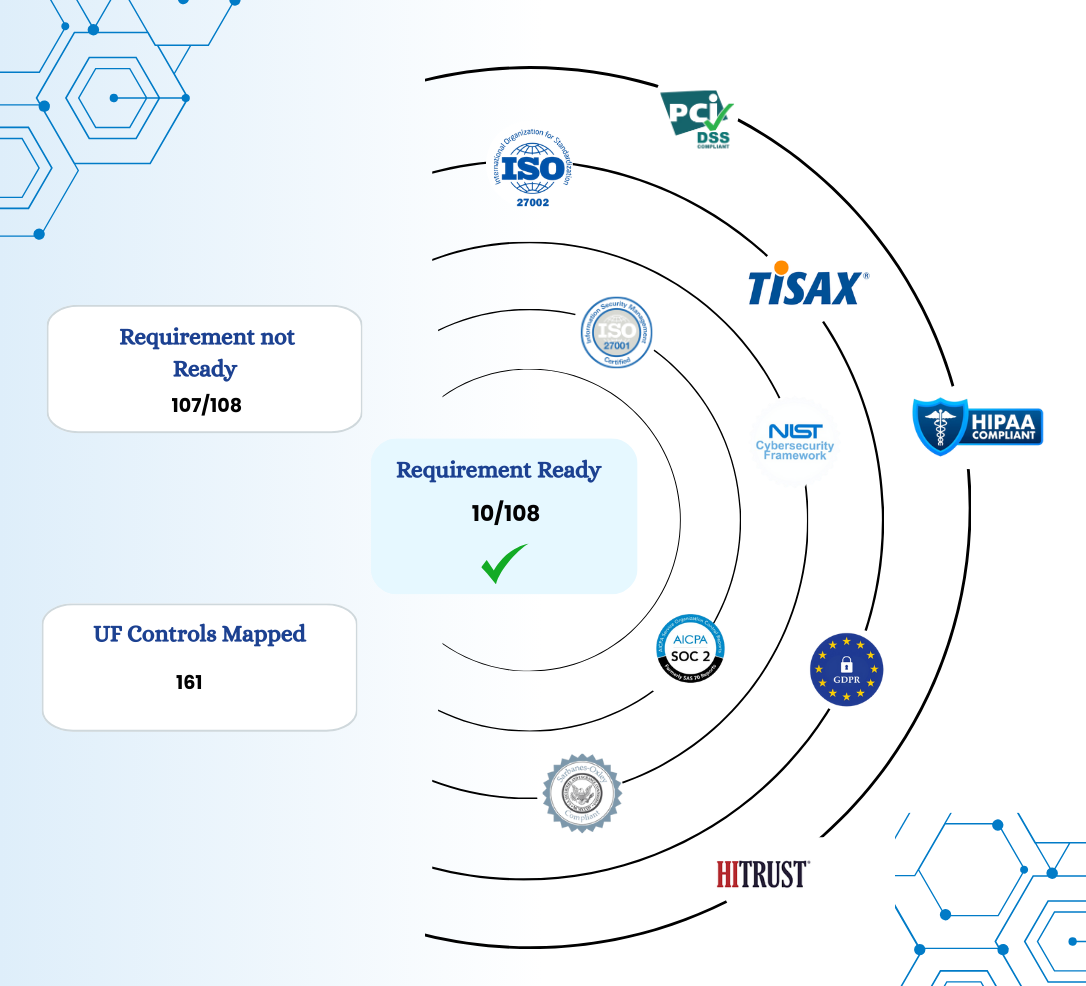
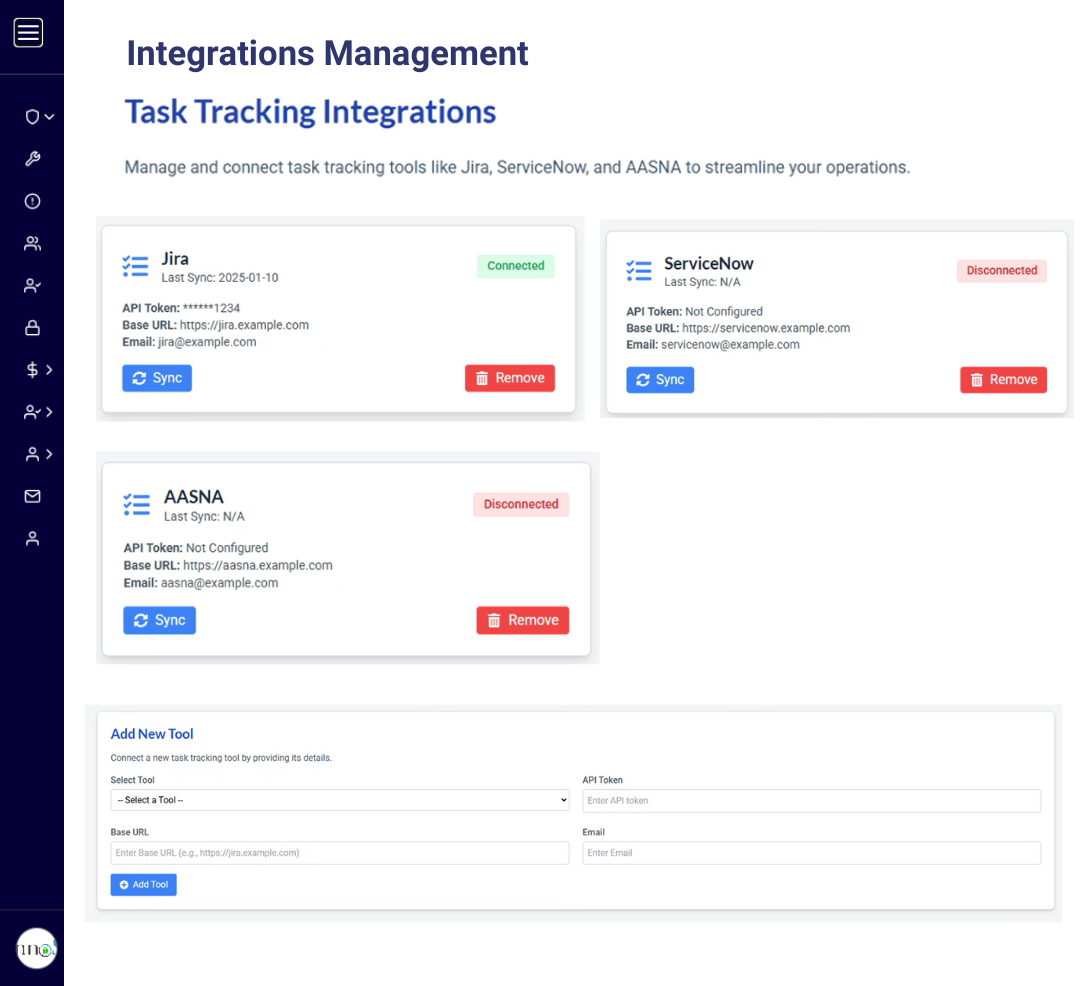
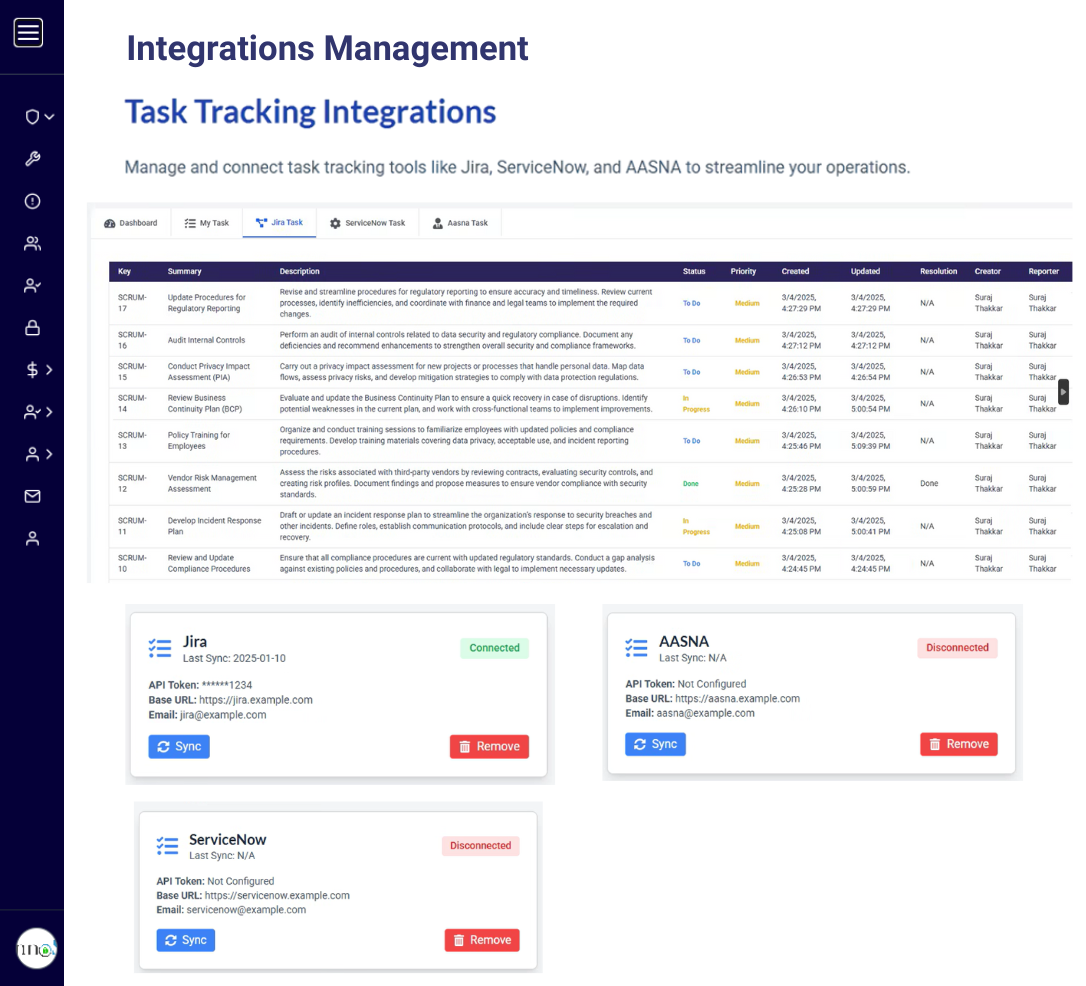
Deep task management at a
category and control level
Deep task management at a category and control level along with dashboards helps to track the tasks, keep schedule, eliminate delays and increased efficiency at reduced costs.
Comply faster, Control
testing and avoid duplication
Regularly test controls on a set schedule to get real-time insights. Highly integrated platform ensure that controls testing could be leveraged for 300+ compliance in real time.
Compatible with all Cloud Connectors
MacOs
Windows
Linux
Android

Firefox
iOS
Chrome
Safari
Related Resources
SOC Management Hub

Thinking about a project?
Get in touch with us.
Connect with Us Today through the Details Below or Fill Out the Form for a Prompt Response

