
Automate HITRUST Compliance to Secure Sensitive Data
GRC³ helps streamline and leverage every compliance and control task performed by your organization to achieve HITRUST CSF certification.
The HITRUST CSF framework integrates various security, privacy, and regulatory requirements, ensuring the protection of sensitive health data and personal information.
GRC³ utilizes existing compliance efforts and control frameworks to enhance HITRUST compliance, driving cost reductions, improving operational efficiency, and expediting the certification process.
Request a DemoEnhance your HITRUST Compliance Journey with Our Advanced Platform
Secure and Scalable
HITRUST-Compliant Storage
Store sensitive data with confidence using our secure, scalable cloud storage solutions that meet HITRUST standards. We offer encrypted storage, fine-grained access controls, and monitoring features to ensure your data is always secure and easily accessible when required for compliance audits.
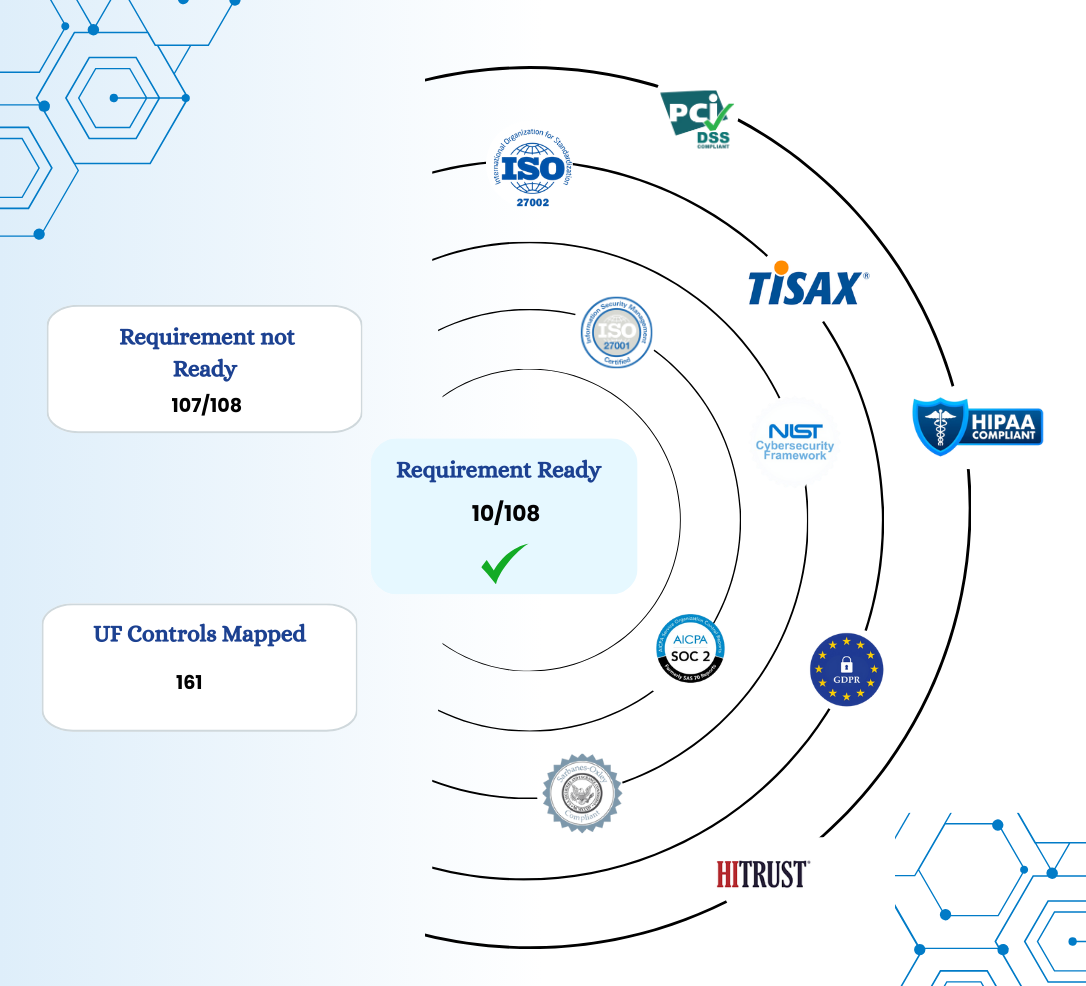
Real-Time Risk Evaluation Reports
Instantly assess your organization’s security posture with detailed risk evaluation reports. These reports provide a comprehensive view of potential risks, gaps, and areas for improvement in your HITRUST compliance efforts, helping you prioritize actions for a more secure environment.
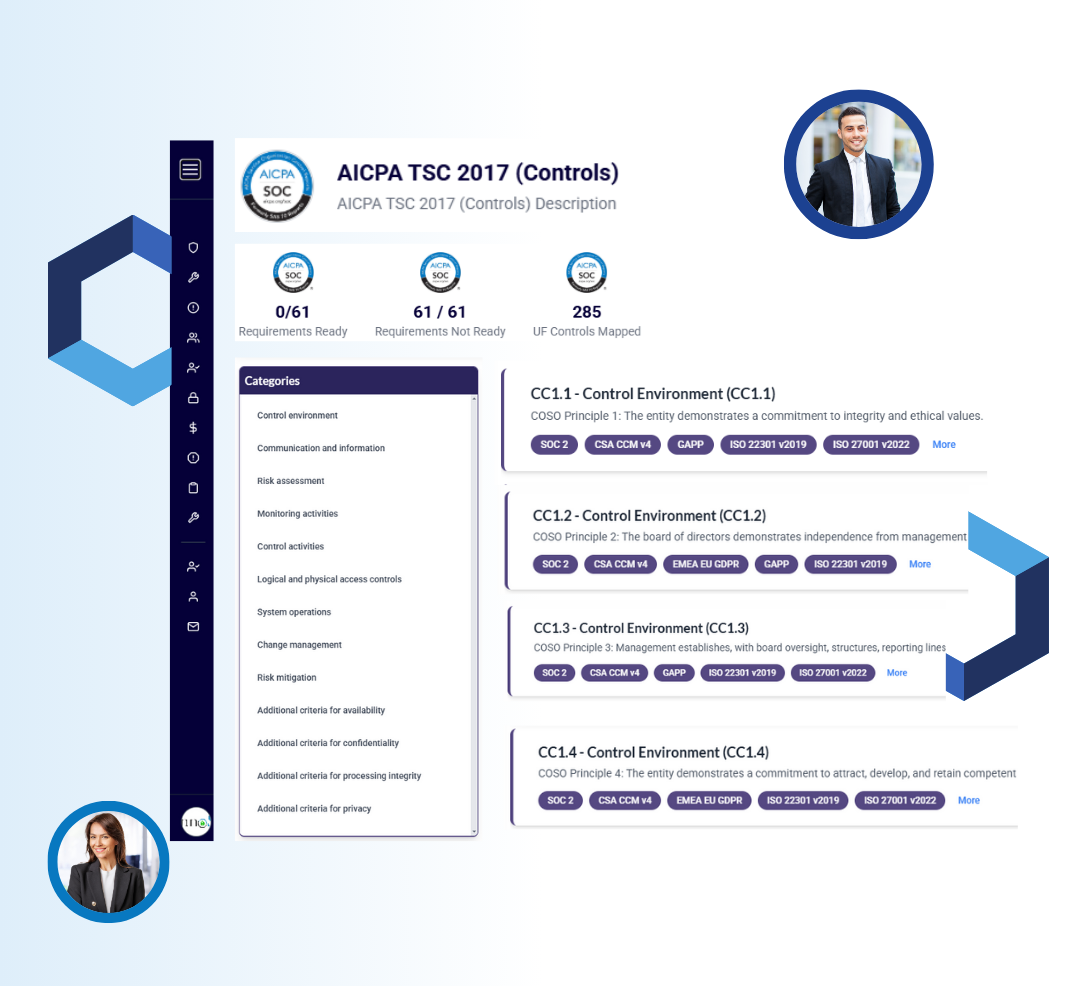
Comprehensive Evidence Management
Our platform simplifies evidence management by automatically collecting and storing proof of compliance. With a user-friendly dashboard, you can efficiently track and manage the controls in place for HITRUST, ensuring all required documentation is readily available when needed.
Insightful Risk Reports
for Continuous Improvement
Generate actionable risk reports that highlight areas requiring attention in your HITRUST compliance efforts. These insights enable your team to strengthen defenses and mitigate vulnerabilities, keeping your organization secure and compliant.
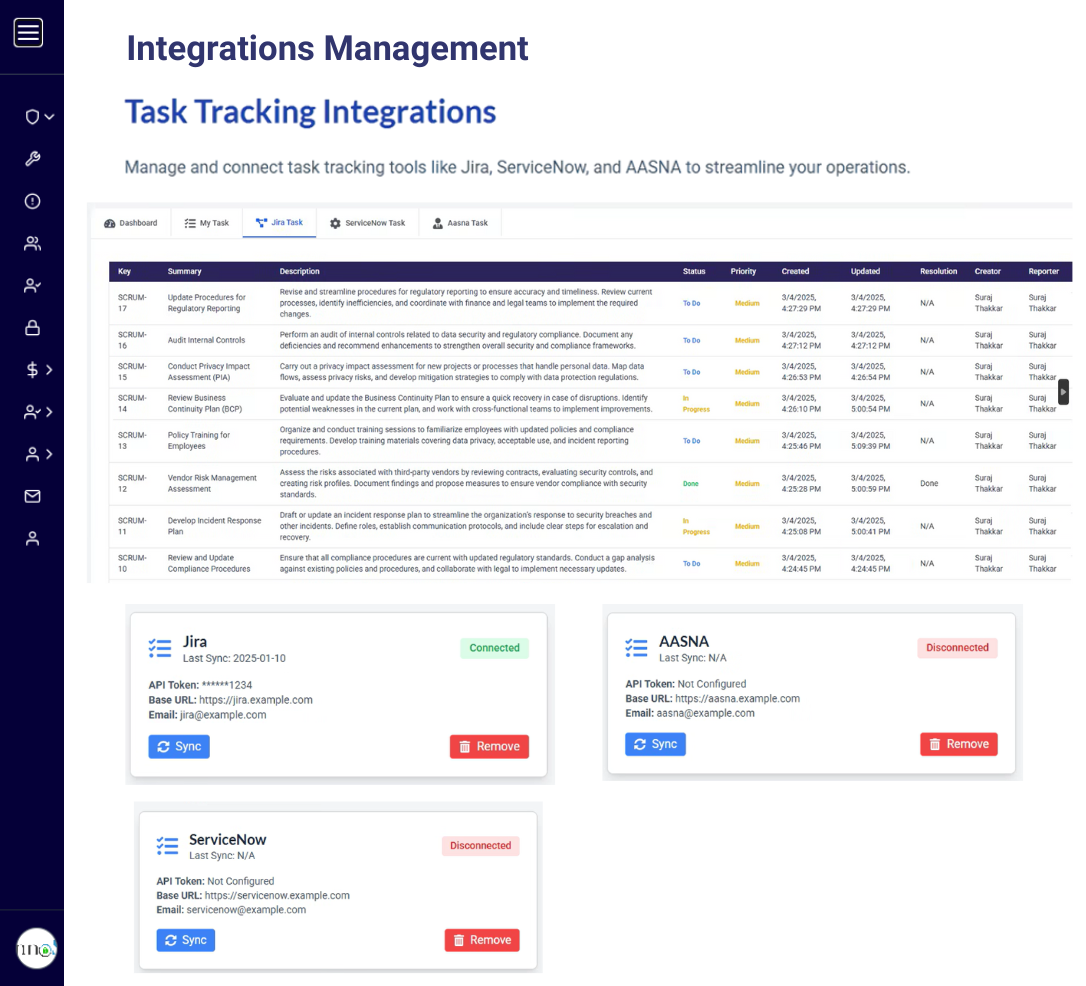
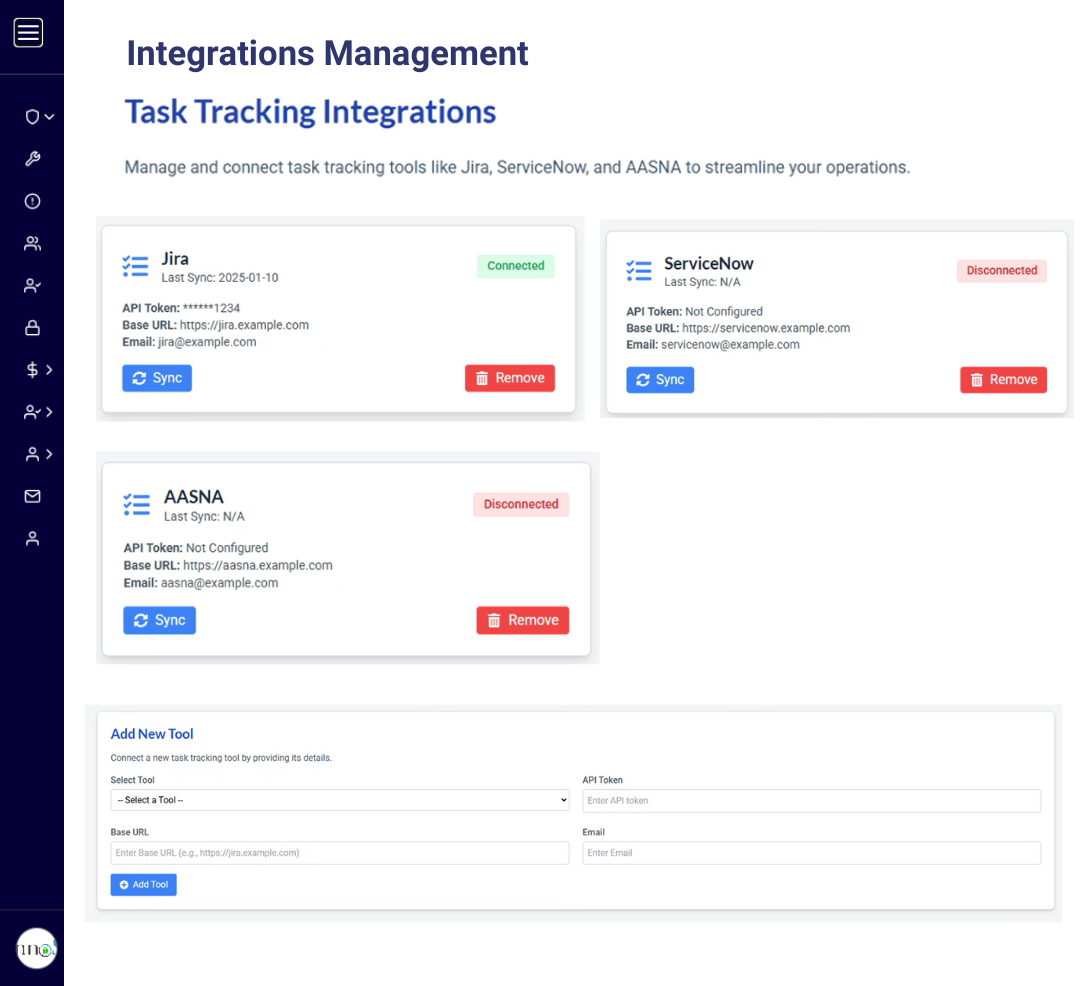
Compatible with all Cloud Connectors
MacOs
Windows
Linux
Android

Firefox
iOS
Chrome
Safari
Related Resources
HITRUST Management Hub

Thinking about a project?
Get in touch with us.
Connect with Us Today through the Details Below or Fill Out the Form for a Prompt Response

