
Achieve CyberSecurity Maturity Compliance with GRC³
With GRC³, you can streamline your efforts towards achieving CMMC compliance by automating processes and ensuring all security controls are mapped and managed seamlessly.
GRC³ provides your team with the tools needed to remain compliant at every stage. Automate compliance tasks, assign individual responsibilities, and easily track progress towards CMMC certification.
Achieve a higher level of cybersecurity maturity and set the foundation for trusted government contracts with GRC³’s comprehensive CMMC compliance tools.
Request a Demo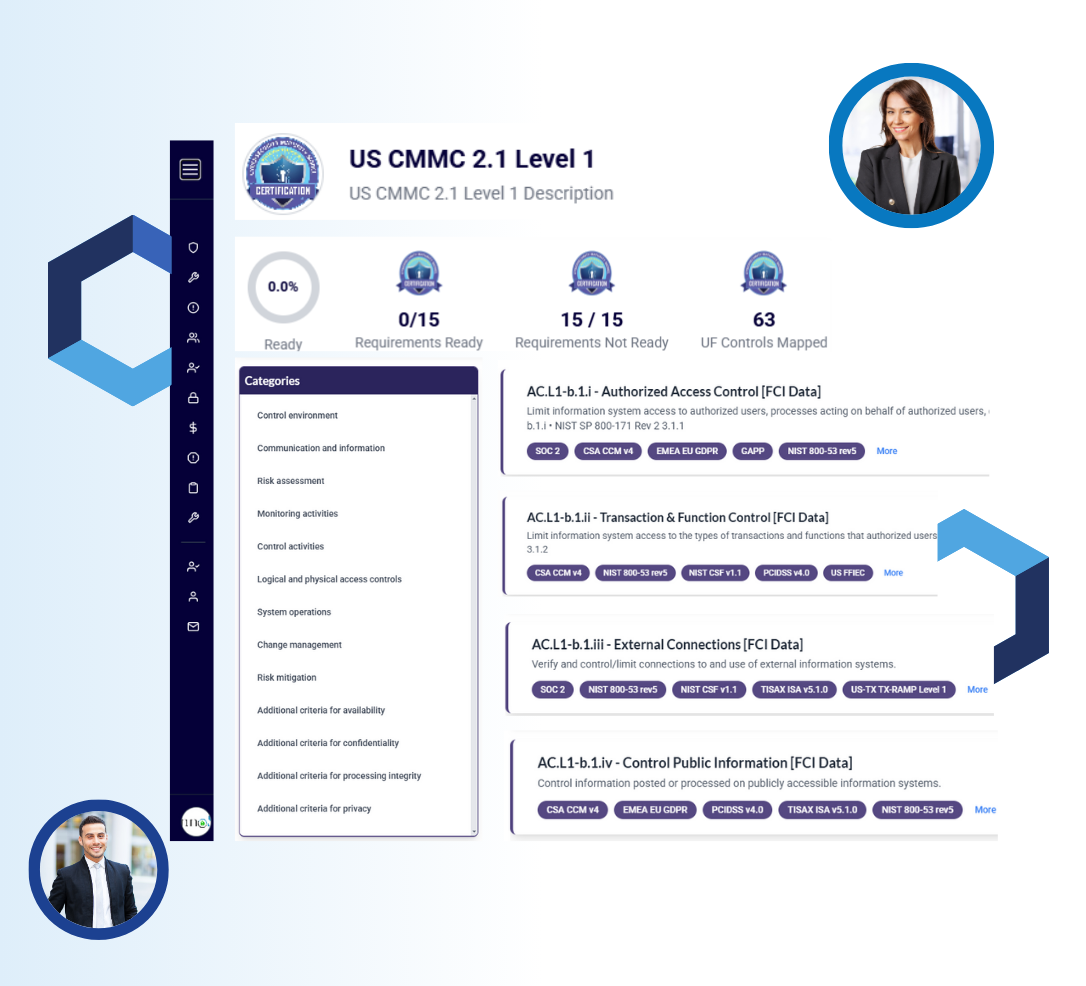
Collect evidence to
prepare for CMMC 2.0 assessment
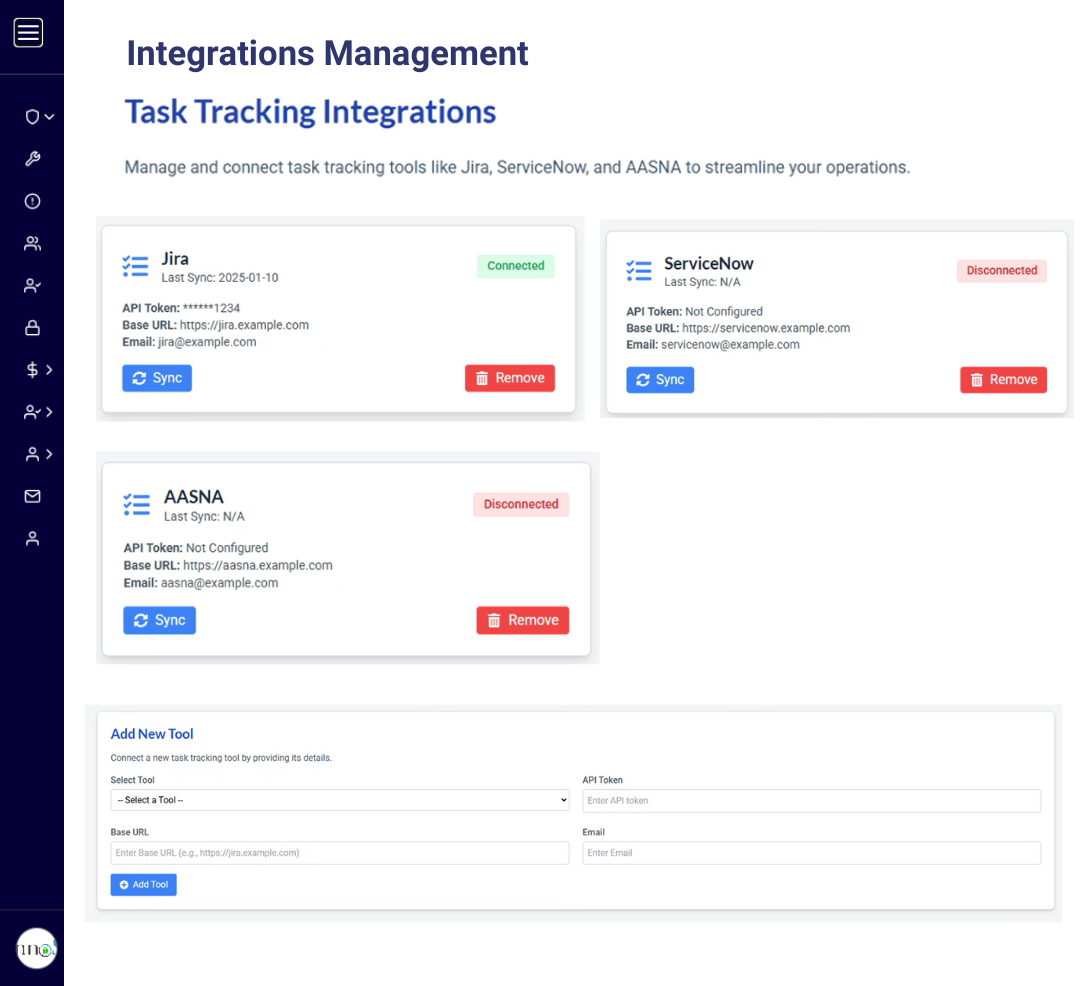
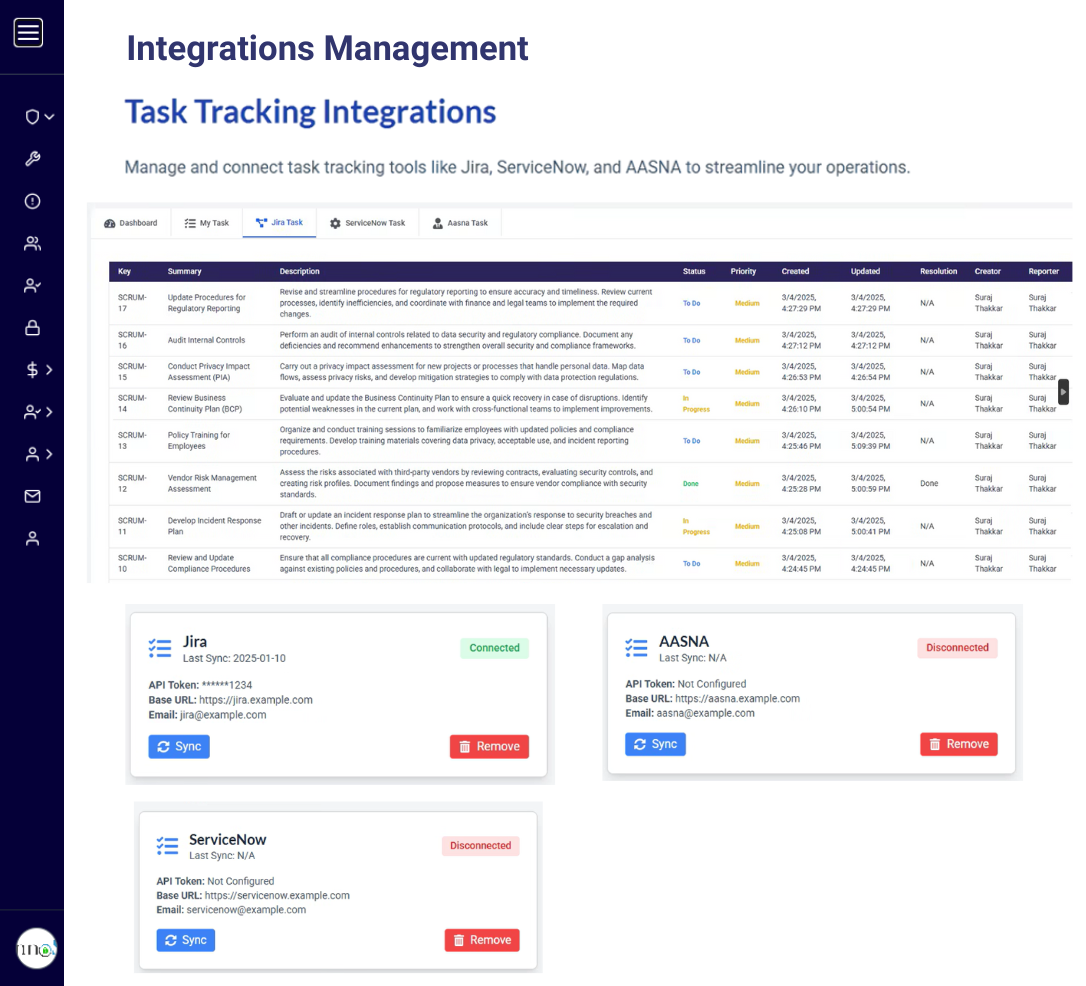
Avoid duplicating work and annoying coworkers by automating evidence collection and ensuring consistent documentation to fulfill assessor requests.
Efficiently manage CMMC 2.0 requirements
GRC³ simplifies CMMC certification by automating cybersecurity control tracking and management. GRC³ helps your organization efficiently meet maturity levels, making compliance easier to manage.
Automated Controls Testing
Regularly test controls on a set schedule to get real-time insights and instant alerts if issues arise.
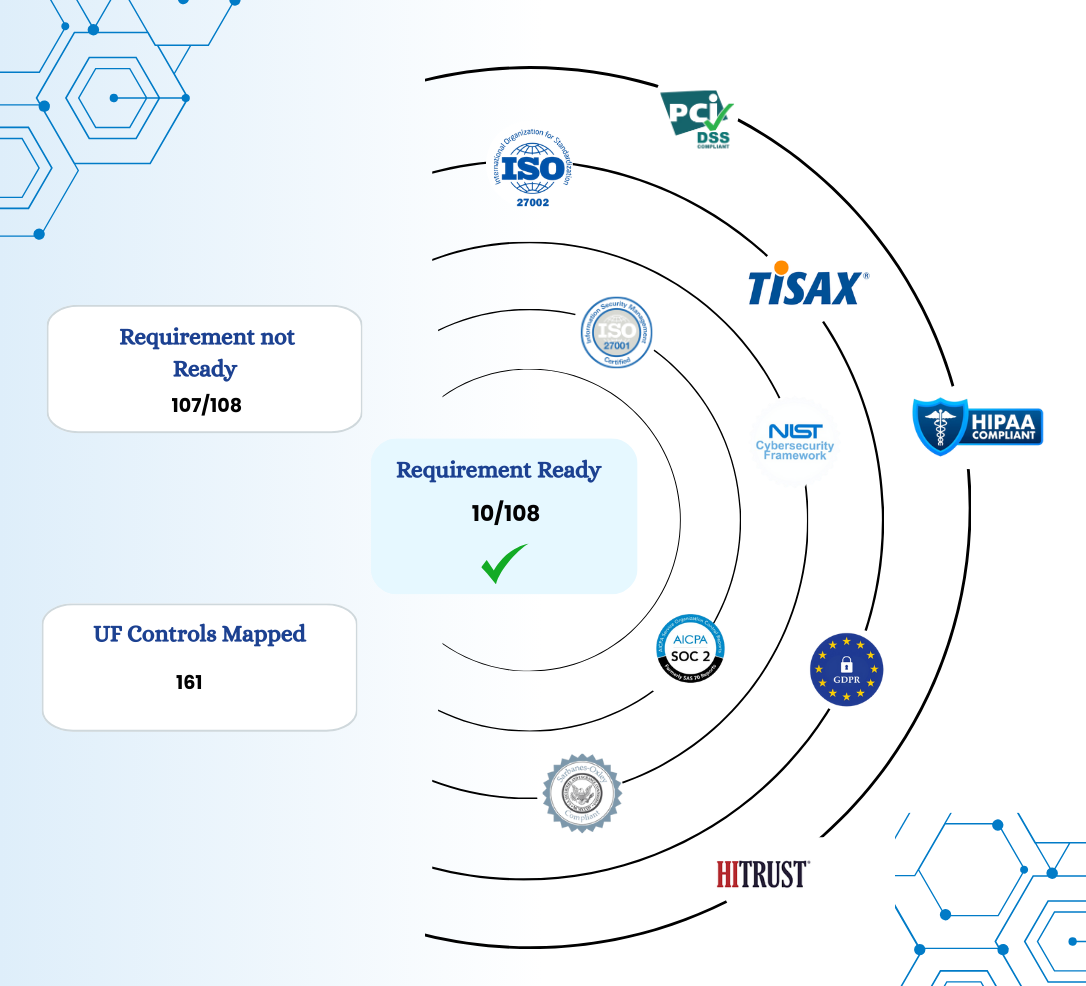
With GRC³ reduce risk and meet CMMC 2.0 requirements
Algorithm has already pre-mapped controls along with testing evidence making it easy to identify the remaining tasks and efforts. Focus on critical security measures with a risk-based model aligned to evolving threats.
Compatible with all Cloud Connectors
MacOs
Windows
Linux
Android

Firefox
iOS
Chrome
Safari
Related Resources
CMMC Management Hub

Thinking about a project?
Get in touch with us.
Connect with Us Today through the Details Below or Fill Out the Form for a Prompt Response

