 Technology
TechnologyInnovations Driving Digital Transformation and Connectivity
Transforming the Future with Technology
Technology is reshaping industries, improving efficiency, and enhancing everyday life through continuous innovation and digital advancements.
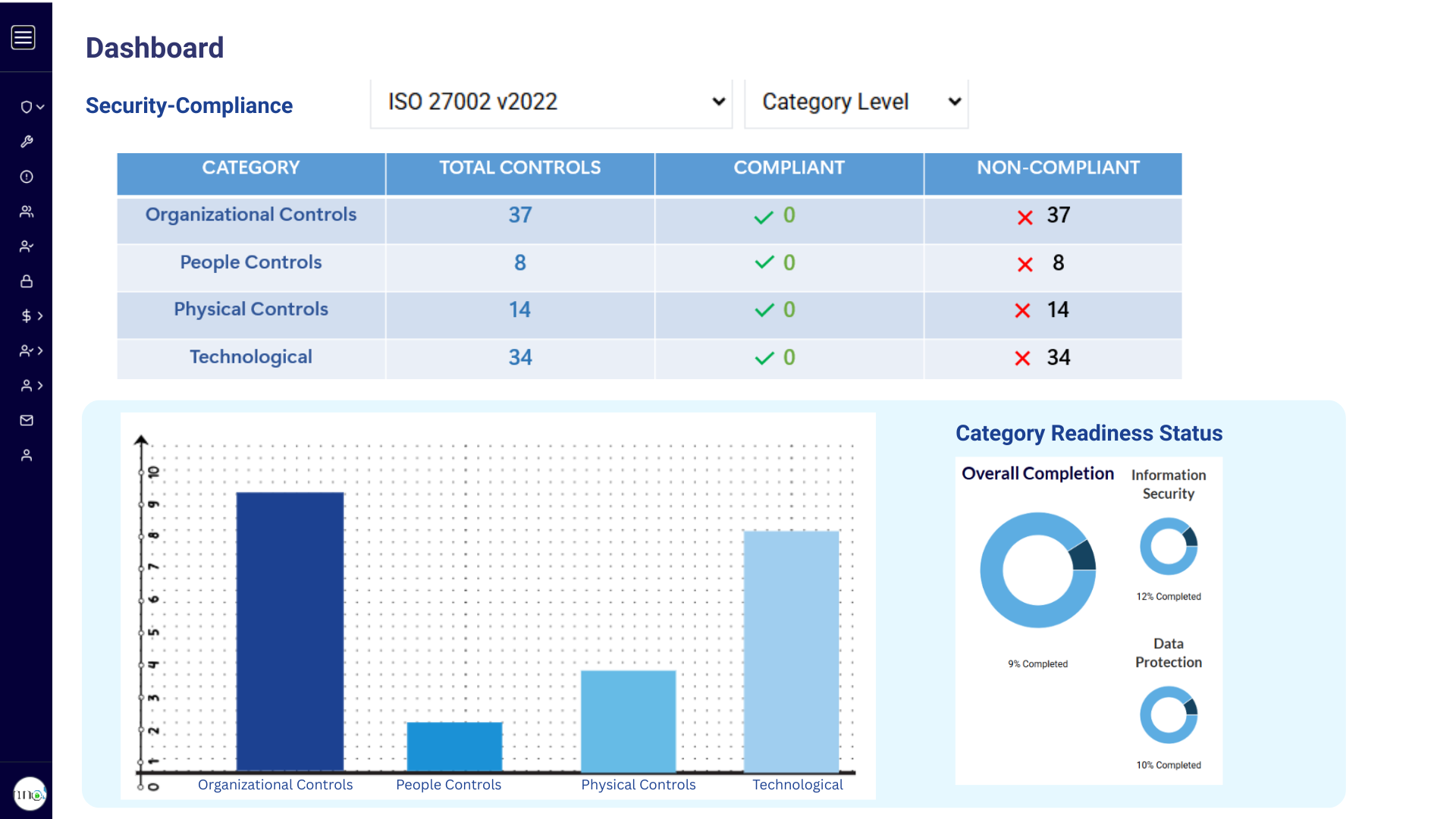
Maintain, Protect, and Reduce Risk with a Compliance and Cybersecurity Strategy
It is common to read news about cybersecurity threats like ransomware, malware, phishing, or IoT-based attacks. 2021 comes with a whole new level of cybersecurity threats. An information report by Threat Horizon states that organizations will face ever-increasing and sophisticated cyber threats under three key themes:
- Disruption (risk of premeditated internet outages that compromise business operations),
- Distortion (spread of misinformation by bots and automated sources), and
- Deterioration (rapid advances in smart technology and conflicting demands posed by evolving national security).
Organizations will be exposed to threats like Cloud Vulnerability, AI-Enhanced Cyber threats, AI Fuzzing, Machine Learning Poisoning, Smart Contract Hacking, and Social Engineering Attacks. Some of the techniques used by attackers will be unknown. The technology solution for the challenges listed above involves rethinking IT security and risk strategy.


Technology
The compliance challenges include ever increasing privacy regulation. The organizations are investing more resources than ever in compliance. There is an overall shortage of qualified cyber security and compliance professionals, hence the organizations need a trusted partner they can team with to help achieve their goals of continually enhancing security and compliance.
e-InnoSec has made significant investments in leadership, methodology, and personnel to be that partner. Our services include free training using the SECURTEAIN eLearning platform as well as classroom training.
Rethink the Security & Risk Strategy
| Cybersecurity Strategy | Cybersecurity Awareness |
| Strong Authentication | Strong Backup |
| Disaster Recovery | Business Continuity |
| Encryption | Vulnerability Management |
| Data Security and Privacy (GDPR, CCPA, and HIPAA) | Regulatory Compliance and Frameworks–NIST CSF, FISMA, ISO, CSA |
| Pen Test | Digital Transformation |
 Services
ServicesGDPR, CCPA, and Privacy State Laws
Helps organizations comply with global and state-specific privacy regulations, ensuring the protection of personal data and user rights.
SOC 1 and SOC 2 Examination
Provides independent audits to assess an organization's controls over financial reporting (SOC 1) and data security, availability, processing integrity, confidentiality, and privacy (SOC 2).
FISMA Compliance
Ensures federal agencies and contractors implement robust security measures to protect sensitive government data, aligning with NIST standards.
PCI Compliance
Ensures businesses securely handle cardholder data by adhering to Payment Card Industry Data Security Standard (PCI DSS) requirements.
Application Security Assessment
Application security assessments identify vulnerabilities and weaknesses in software, ensuring robust protection against cyber threats and data breaches.
Threat Modelling, Vulnerability Management, and Pen Test
Threat Modeling, Vulnerability Management, and Pen Test A proactive approach to identifying, assessing, and mitigating security risks through structured threat analysis, continuous vulnerability management, and penetration testing.