 Malware/Ransomware
Malware/RansomwareTHE NUMBER 1 IN GOVERNANCE, RISK, AND COMPLIANCE MANAGEMENT
Strengthen Security Resilience and Combat Malware/Ransomware Threats With GRC³
Boost your organization's security with a powerful platform that detects, prevents, and mitigates malware and ransomware attacks. Focus on your success while we handle the threats.
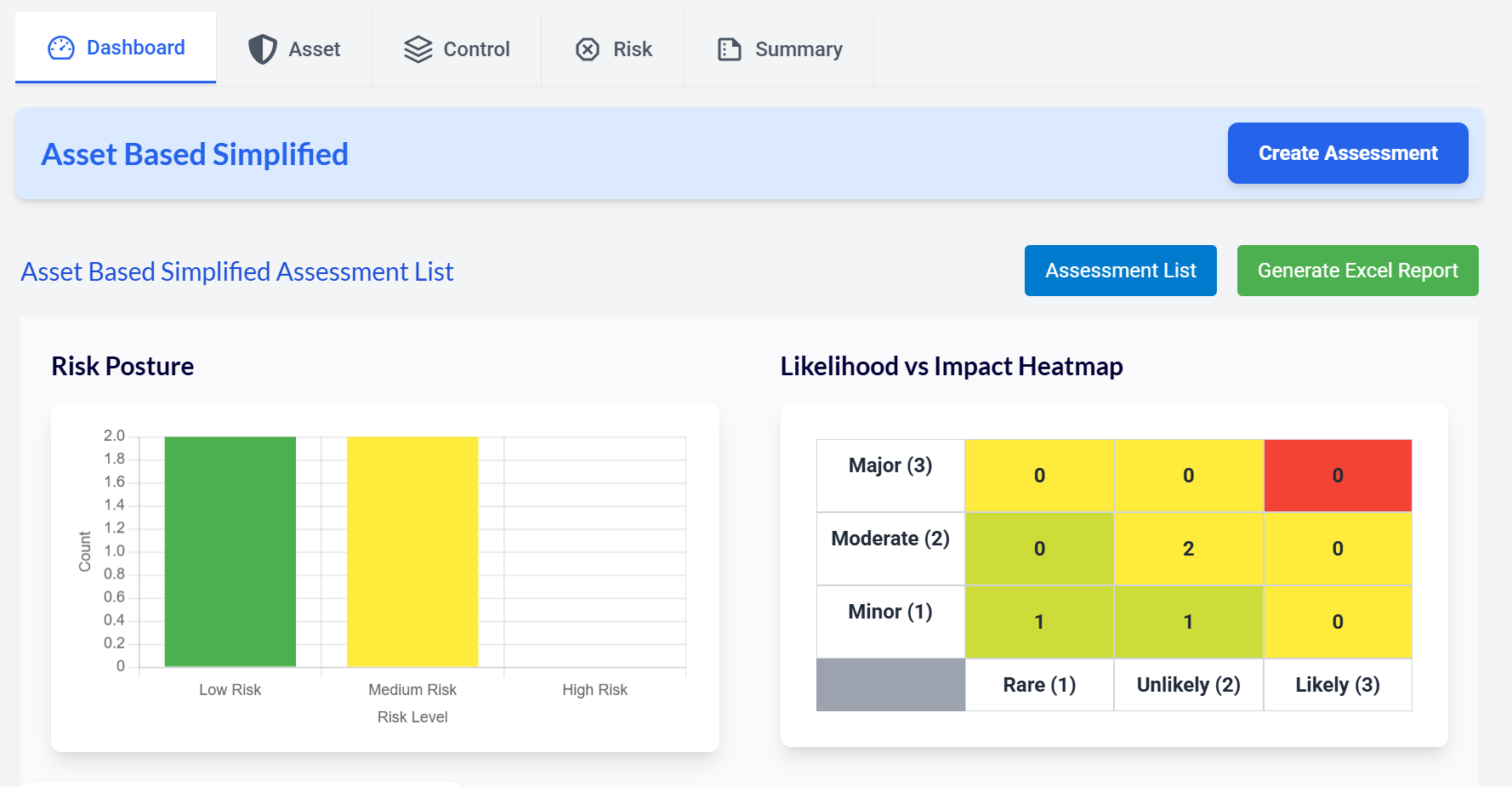
Why Malware/Ransomware Protection?
Ransomware is one of the most costly and disruptive cybersecurity threats. This type of cyberattack is on the rise in the United States, with 59% of all ransomware attacks taking place there.
The average cost of a single ransomware attack is $1.85 million.
Kaspersky Says 70% of Organisations Struggle to Keep Up with the Volume of Security Alerts.
Malware/Ransomware Protection
Enhance your defenses, detect threats in real time, and ensure quick recovery with a comprehensive platform for malware and ransomware protection.
Threat Detection & Prevention
Identify and block potential malware and ransomware threats proactively, employing advanced detection methods and AI algorithms to prevent harm.
Real-Time Threat Monitoring
Regularly monitor your network and systems to detect and address threats as they happen, enabling prompt action against suspicious activity.
Incident Response & Recovery
Respond quickly to security incidents with an incident management system that helps you contain issues, recover faster, and reduce downtime.
Automated Incident Response
Utilize automated workflows to swiftly contain, isolate, and neutralize threats with minimal human intervention, thereby reducing response time.
Security Monitoring & Analytics
Stay proactive by monitoring your network and endpoints in real-time. Use alerts and analytics to outsmart emerging risks.
Continuous Network Surveillance
Utilize monitoring tools to continuously track network traffic and system logs, detecting anomalies and potential threats before they escalate.
Compliance & Risk Management
Align cybersecurity practices with industry standards (GDPR, HIPAA, NIST) to minimize legal and financial risks.
Regulatory Alignment
Implement cybersecurity practices that comply with industry regulations, including GDPR, HIPAA, and NIST, to minimize legal and financial risks.
 Advanced Features
Advanced FeaturesCutting-Edge Tools to Detect, Prevent, and Mitigate Evolving Cyber Threats
AI-Powered Threat Detection
Leverage machine learning and artificial intelligence to detect emerging threats, recognizing malware and ransomware patterns without prior knowledge of an attack. This proactive approach empowers organizations to prevent significant damage before it occurs.
Real-Time Threat Intelligence
Continuously analyze global threat intelligence to provide current insights into malware tactics, techniques, and procedures (TTPs), helping organizations stay ahead of cybercriminals and strengthen their defenses.
Behavioral Threat Analysis
Monitor and analyze system and user behavior to detect anomalies that may indicate malicious activity. By prioritizing behavioral analysis over traditional detection methods, organizations can proactively identify new and unknown threats early on
Automated Incident Workflows
Respond swiftly to ransomware attacks with automated workflows that isolate infected systems, prevent the spread of malware, and initiate remediation efforts. This approach reduces the risk of human error and accelerates recovery.
Endpoint Detection & Response
Implement advanced Endpoint Detection and Response (EDR) solutions that monitor and respond to suspicious activities on endpoints in real time. This ensures that malware is detected and contained at its source before it can infiltrate deeper into the network.
Ransomware Recovery & Rollback
Utilize integrated backup and rollback features that allow businesses to quickly restore encrypted files or systems to a pre-attack state. This minimizes downtime and financial losses, ensuring that systems are back online swiftly.
Related Resources
Malware Ransomware Management Hub



