 Healthcare Services
Healthcare ServicesEnsuring Secure, Efficient, and Compliant Healthcare Solutions for Improved Patient Outcomes
With Innovation and Security transforming Healthcare Services
Leveraging advanced technology, regulatory compliance, and secure solutions to enhance patient care, streamline operations, and ensure data privacy in the healthcare industry.
Simplifying Compliance and Transforming Cybersecurity for Healthcare
While cybersecurity threats continue to increase in healthcare, the sheer volume of attacks represents the cybercriminal’s creative skills to devise novel ways to breach defenses through increasingly targeted and sophisticated attacks.
The rise of security incidents, such as the notorious ransomware WannaCry or the recent proliferation of cryptocurrency coin miners, are a timely reminder that the volume of attacks increasing. A few examples of attacks:
- Ransomware/malware attack breaches 45,000 patient records: July 26, 2018
- LabCorp's network breach puts millions of records at risk: July 17, 2018
- Patient data exposed for months after phishing attack on Sunspire: July 18, 2018
- Phishing attacks breach Alive Hospice for 1 to 4 months: July 18, 2018
- Malware attack on UVA Health gave hacker access for 19 months: February 22, 2018
Healthcare management devices with high definition technology allow them to interact with the internet and be managed remotely. These Internet of Things (IoT) devices are integrated with technology like sensors and functional software that allows machine-to-machine interaction. The insecure IOT devices provide an easy gateway for cybercriminals to get inside the network.
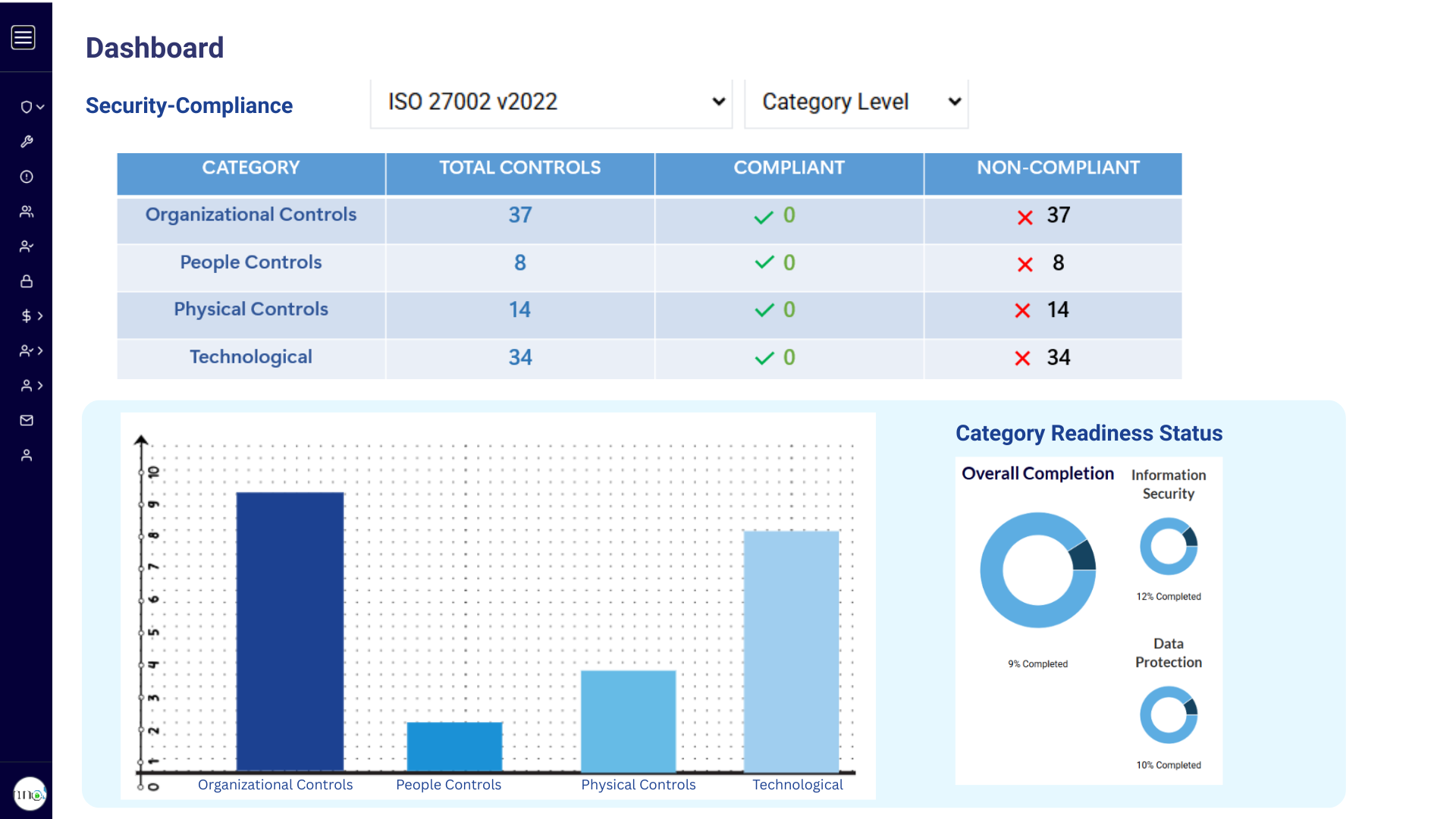
Compliance challenges include new and changing health care laws and privacy requirements (MACRA, ACA, HIPAA, GDPR, CCPA, State Laws, etc.). HIPAA compliance continues to be a high priority issue. Not just cybersecurity officers but compliance officers are also looking for ways to increase efficiency and reduce risk.


Healthcare and Life Sciences Services
Technological innovation and cybersecurity threats continue to develop and evolve at an incredible pace. Hospitals, prominent corporations, and even city governments have fallen victim to sophisticated ransomware attacks in recent years. Healthcare management providers need to view cybersecurity as a business risk rather than just a technical challenge and need immediate improvements to address these new risks. Healthcare organizations are investing more resources than ever on compliance. There is an overall shortage of qualified cybersecurity and compliance professionals; hence organizations need a trusted partner to team with to help achieve their goals of continually enhancing patient data privacy and security.
e-InnoSec has made significant investments in leadership, methodology, and personnel to be that partner. The services include free training using the SECURTEAIN eLearning platform as well as classroom training.
 Services
ServicesHIPAA/HITECH Compliance
Ensure the protection of sensitive healthcare data by meeting HIPAA and HITECH regulatory requirements for security and privacy.
Readiness and Certification Services
Prepare your organization for industry certifications with structured assessments, gap analysis, and compliance roadmaps.
PCI DSS Compliance
PCI DSS Compliance refers to the set of security standards designed to protect card payment information from fraud and breaches. Organizations handling credit card data must meet these standards to ensure secure transactions and data protection.
Vulnerability Management and Pentest
Vulnerability Management is the process of identifying, evaluating, and mitigating security weaknesses in systems, while Penetration Testing (Pentest) simulates cyberattacks to find exploitable vulnerabilities before malicious hackers can exploit them.
GDPR and CCPA Services
GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) services help organizations comply with data privacy laws by ensuring proper handling, protection, and transparency of personal data for EU and California residents, respectively.
Software Selection – ERP, Cyber Tools, HRIS, etc.
Software selection involves choosing the right tools for business needs, such as ERP (Enterprise Resource Planning) systems for business operations, cybersecurity tools for protection, and HRIS (Human Resource Information Systems) for managing employee data and HR processes.