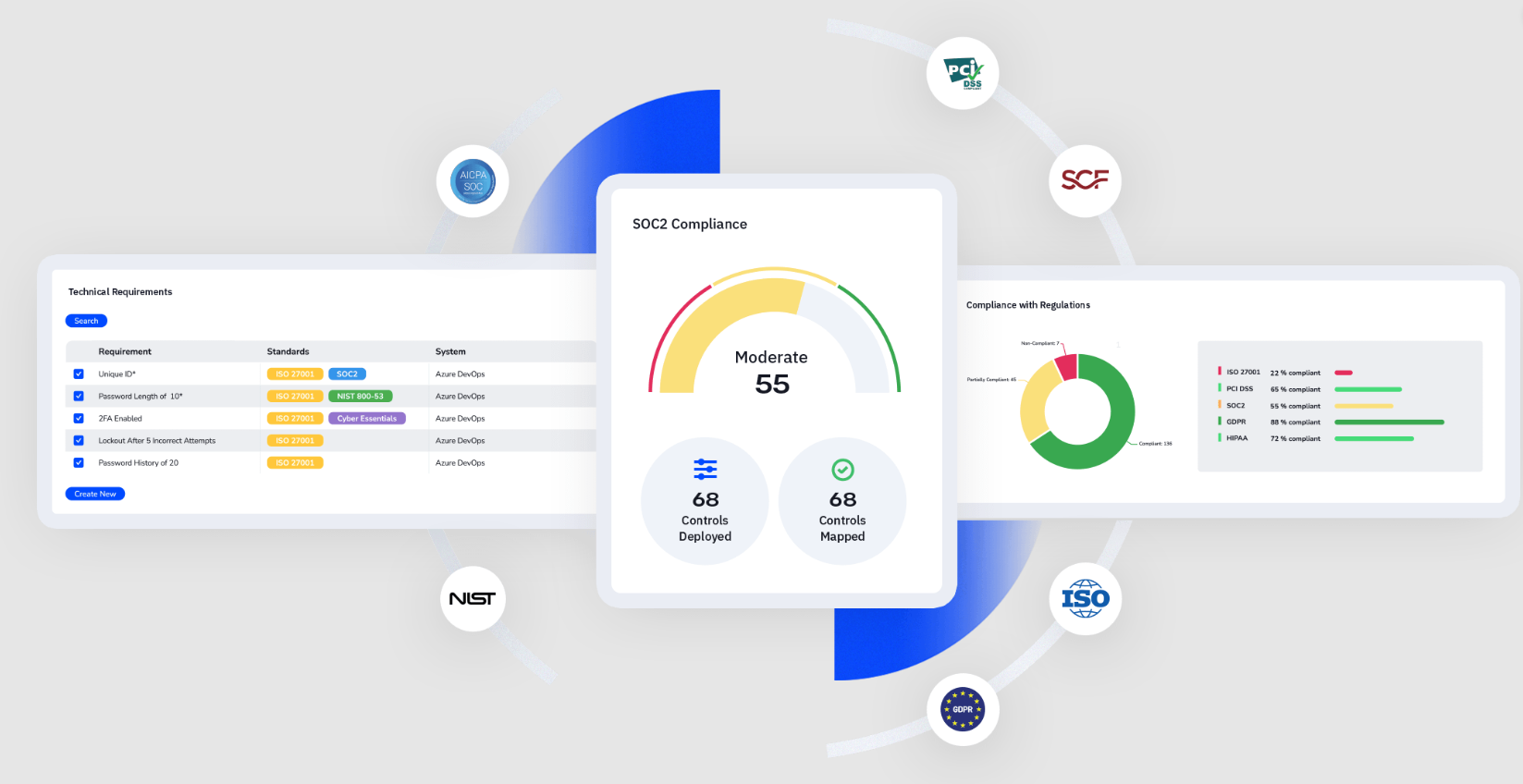
What we offers
What we offersThe Largest Framework Library on the Market
As your company’s needs change, your compliance needs evolve. e-GRC extensive risk management and compliance framework library of over 300+ framework templates with requirements and controls can be fully
customized to your organization.
Trusted by great companies
INTEGRATE NEW AND EXISTING FRAMEWORKS
SEAMLESSLY
Strike Graph instantly connects your existing controls and evidence to any new framework you enable in the
platform — drastically reducing the time and expense of adding new frameworks.

ISO 27001
ISO 27001 is an information security management system (ISMS) that helps keep consumer data safe.

ISO 27002
ISO 27002 provides guidelines for applying ISO 27001 effectively and improving your information security practices.

PCI DSS
PCI DSS ensures secure handling of cardholder data by organizations to protect against data breaches and fraud.

GDPR
GDPR is a regulation in EU law on data protection and privacy in the European Union and the European Economic Area.

SOC 2
SOC 2 defines criteria for managing data based on: security, availability, processing integrity, confidentiality, and privacy.

NIST
NIST is the set of cybersecurity activities and desired outcomes common across any critical infrastructure sector.

HIPAA
HIPAA is a U.S. regulation that ensures the security and privacy of healthcare information, applicable to healthcare providers and related organizations.

FEDRAMP
FEDRAMP is a U.S. government framework for assessing and authorizing cloud service providers to ensure they meet strict security requirements.

CMMC
CMMC is a framework introduced by the U.S. Department of Defense to ensure cybersecurity practices in the defense supply chain.

COBIT
COBIT is a framework for IT governance and management, helping organizations align IT goals with business objectives while mitigating risks.

CIS Controls
CIS Controls are a prioritized set of cybersecurity best practices, helping organizations defend against common threats through actionable steps.

SOX (Sarbanes-Oxley Act)
SOX (Sarbanes-Oxley Act) is a U.S. law that focuses on financial data security and governance, with IT-related sections emphasizing the protection of electronic records.

All Supported Frameworks
Comprehensive and Customizable
Explore the extensive list of supported frameworks for your compliance needs.
Information Security
- ISO 27001Information Security Management System
- NISTNational Institute of Standards and Technology
- COBITControl Objectives for Information Technologies
- NIST SCFNIST Secure Controls Framework
- SOC 1System and Organization Controls 1
- TISAXTrusted Information Security Assessment Exchange
- SOC 2System and Organization Controls 2
- SOC 3System and Organization Controls 3
- NIST 800-53Security & Privacy Controls
- MSRMinimum Security Requirements = MCR + DSR
- CJISCriminal Justice Information Services Security Policy
- ISO 42001ISO 42001 Standards
- ISO 20000 ISO 2001 Standards
- ISO 27799 ISO 27799 Standards
- NIST AI 600-1 NIST Artificial Intelligence Framework
- NIST 800-171 Protecting Controlled Unclassified Information
- NIST SP 800-218A Secure Software Development Framework
- ISO/SAE 21434 v2021 ISO 21434 Standard
- ISO 22301 v2019ISO 22301 Standard
- ISO 27001 v2022ISO 2022
- ISO 42001 v2023ISO 42001 Standard
- NIST 800-37 rev 2NIST 800-37 Revised 2 Framework
- NIST 800-53 rev 5NIST 800-53 Revised 5 Framework
- NIST 800-82 rev 3 LOWNIST 800-82 Revised 3 Framework
Privacy
- CCPACalifornia Consumer Privacy Act
- CPRACalifornia Privacy Rights Act
- eIDASElectronic Identification and Trust Services
- FERPAFamily Educational Rights and Privacy Act
- GDPRGeneral Data Protection Regulation
- GLBAGramm-Leach-Bliley Act
- Guernsey DPLGuernsey Data Protection Law
- IRS 1075Internal Revenue Service Publication 1075
- IRS 4812IRS Safeguards for Taxpayer Information
- MARS-EMinimum Acceptable Risk Standards for Exchanges
- PCIDSS v3.2Payment Card Industry Data Security Standard v3.2
- PCIDSS v4.0Payment Card Industry Data Security Standard v4.0
- Mastercard TQMMastercard Terminal Quality Management
- PCI DSSPayment Card Industry Data Security Standard
- PCI DSS v4.0 SAQ A Payment Card Industry Data Security Standard
- PCI DSS v4.0 SAQ AE-P Payment Card Industry Data Security Standard
- PCI-P2PEPoint-to-Point Encryption Standard
- PCI-PINPIN Security Requirements
- PCI-POIPoint of Interaction Security Requirements
- PHIPA OntarioPersonal Health Information Protection Act
- PIPA AlbertaPersonal Information Protection Act (Alberta)
- PIPA BCPersonal Information Protection Act (British Columbia)
- PIPEDAPersonal Information Protection and Electronic Documents Act
- USA PATRIOT ActUniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism Act
Cybersecurity
- CIS ControlsCenter for Internet Security Controls
- Essential EightAustralian Cybersecurity Practices
- DORADigital Operational Resilience Act
- NCSC CAFNational Cyber Security Centre Cyber Assessment Framework
- CIS CSC v8.0CIS Critical Security Controls Version 8
- CIS CSC v8.0 IG1Implementation Group 1 for CIS Critical Security Controls v8.0
- CIS CSC v8.0 IG2Implementation Group 2 for CIS Critical Security Controls v8.0
- CIS CSC v8.0 IG3Implementation Group 3 for CIS Critical Security Controls v8.0
- ENISA v2.0European Union Agency for Cybersecurity Framework v2.0
- MITRE ATT&CK 10MITRE Adversarial Tactics, Techniques, and Common Knowledge Version 10
- SPARTASecurity & Privacy Assurance Research & Technology
- US CMMC 2.0 Level 1 Cybersecurity Maturity Framework
Health
- HIPAAHealth Insurance Portability and Accountability Act
- HITRUST CSFHITRUST Common Security Framework
- HITECH ActThe Health Information Technology for Economic and Clinical Health Act
- ICH GCPInternational Council for Harmonisation Good Clinical Practice
Financial
- GFSC Handbook Guernsey Financial Services Commission Handbook
- SOX Sarbane-Oxley-Act
Quality Management
- ISO 13485 ISO 13485 Standard
- ISO 9001 ISO 9001 Standard
Environmental Management
- ISO 14001 Environmental Management
BCP
- ISO 22301 Business Continuity Management Systems
- HITRUST CSF HITRUST Common Security Framework
Conformity Assessment
- ISO 14001 ISO 14001 Standard
 What we offers
What we offersThe Leading IT Solutions
Company For You
What We Do
Custom Services For
Your Business
It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
Creative Ideas
Web Development
Digital Marketing
App Development
See why we are
trusted the world over
New accounts
Finished projects
Skilled experts
Media posts
 OUR TEAM MEMBERS
OUR TEAM MEMBERSMeet Our Team
Meet the talented and passionate team members who drive our company forward every day.
company forward every day.
Core values
We break down barriers so teams can focus on what matters – working together to create products their customers love.
Genuine repeated
happy customers.
Genuine repeated
happy customers.
Customers First
Our company exists to help merchants sell more. We make every decision and measure every outcome based on how well it serves our customers.
Think Big
Our company exists to help merchants sell more. We make every decision and measure every outcome based on how well it serves our customers.
Make a Difference
Our company exists to help merchants sell more. We make every decision and measure every outcome based on how well it serves our customers.
Act With Integrity
Our company exists to help merchants sell more. We make every decision and measure every outcome based on how well it serves our customers.
Do the right thing
Our company exists to help merchants sell more. We make every decision and measure every outcome based on how well it serves our customers.
Stronger united
Our company exists to help merchants sell more. We make every decision and measure every outcome based on how well it serves our customers.
 Download Mobile App
Download Mobile AppManage all from anywhere
⚡Don't miss any contact. Stay connected.
Genuine
happy customers.
Happy
Customers
Consultation
Completed

Loved by over 4k
happy clients
We Provide Best IT Services For Your Need
It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout.
Getting started is simple! Download the app from the App Store or Google Play Store, create an account using your email or social media login, and start making video calls instantly.
Getting started is simple! Download the app from the App Store or Google Play Store, create an account using your email or social media login, and start making video calls instantly.
Getting started is simple! Download the app from the App Store or Google Play Store, create an account using your email or social media login, and start making video calls instantly.
Getting started is simple! Download the app from the App Store or Google Play Store, create an account using your email or social media login, and start making video calls instantly.
Getting started is simple! Download the app from the App Store or Google Play Store, create an account using your email or social media login, and start making video calls instantly.
 working process
working processHow It Works
Comprehensive Suite of Cutting-Edge IT Services.
Choose Services
It is a long established fact that a reader will be distracted by the readable content of a page.
Project Analysis
It is a long established fact that a reader will be distracted by the readable content of a page.
Got Final Result
It is a long established fact that a reader will be distracted by the readable content of a page.
Need more help? Go to our Support Center

 What we offers
What we offersLooking to speak with a marketing specialist?
Our seasoned marketing specialists are here to help! Whether you need insights on digital campaigns, social media tactics, or overall branding, our experts offer tailored advice to meet your specific needs.
 From Blog
From Blog